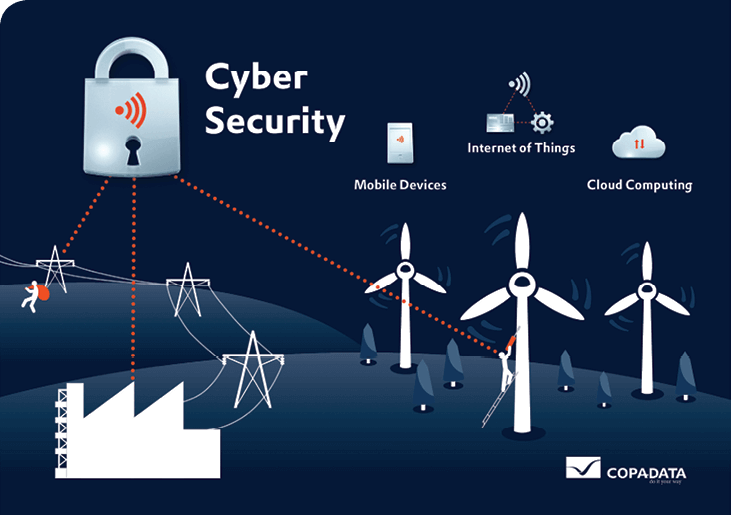
Solar energy technologies can be vulnerable to cyberattack through inverters and control devices that are designed to help manage the electric power grid. Operating-technology (OT) devices like solar photovoltaic inverters, when connected to the Internet, are at higher risk relative to stand-alone OT devices. They must be able to prevent, detect, and respond to unauthorized access or attack. While some cyberattacks manipulate information-technology (IT) systems, cyberattacks on electric-grid devices can cause physical impacts like loss of power and fires.
The electric grid is becoming increasingly digitized and connected, so maintaining cybersecurity is a top priority for the U.S. Department of Energy (DOE). There are daily attempts to attack the grid, but the majority are not successful. In March 2019, however, hackers breached a utility’s web-portal firewall, causing operators to lose visibility of parts of the grid intermittently for 10 hours.
What is a Cyber Attack?
You may envision lone hackers furiously entering commands in dark rooms, illegally breaching and controlling sensitive systems, but many cyberattacks are more ordinary. For example, phishing scams use emails that appear to come from reputable sources and trick people into giving important information to a malicious actor. This type of manipulative, fraudulent practice is called social engineering. Failure to recognize such deceptions is the entry point into many systems.
Outdated software is another risk: A novice hacker could take advantage of a system’s known vulnerabilities by running code downloaded from the Internet to attack it. Advanced hackers might discover problems so new that they’re called “zero-day attacks,” meaning security professionals have had no time to prepare for them.
A cyberattack on a cyber-physical system is different from one on an enterprise IT system because of the physical consequences. Cyber-physical systems are engineered systems that are built from, and depend upon, the seamless integration of computation and physical components.
How Could Hackers Attack Solar Power Systems?
Historically, cyber risk for solar was relatively minor, given how few systems were deployed and because most solar inverters did not communicate for monitoring or control. However, as more solar is installed and inverters become more advanced, this risk grows. Inverters are the interface between solar panels and the grid. If the inverter’s software isn’t updated and secure, its data could be intercepted and manipulated. An attacker could also embed code in an inverter that could spread malware into the larger power system.
A cyberattack that introduces instabilities or false information into the power system can cause physical as well as financial damage. For example, a security breach could make an unauthorized change in power delivery. Unauthorized changes to inverter controls or communications like these are called cyber-physical security breaches, because the result is a change in the voltage or the electric current that the inverter injects into homes or the grid.
Microgrids are also a potential target for cyberattacks. Microgrids are local power systems that can operate independently of the larger grid in case of a power outage. Protecting them from cyberattack becomes part of an overall resilience strategy to maintain critical electrical infrastructure in emergencies.
Managing Vulnerabilities
The introduction of widespread digitization and interconnectivity across the modern grid presents a great challenge for grid operators. As more solar and other distributed energy resources (DER) are added to the grid, so are more tools that provide utilities with real-time solar power generation and other information. These tools must be secured, or the grid will become more vulnerable to cyberattack.
Security software can help utilities maintain control of their DER and prevent attackers from injecting false information into the system. Most attempted attacks on the grid are mitigated by intrusion-detection software that alerts grid operators to abnormal behavior.
Utilities and solar system owners and operators can use a dynamic survival strategy based on defense-in-depth measures, which are basically diverse layers of security that cover everything from individual components to entire systems. For example, installing anti-virus software in DER systems, such as solar inverters and battery controllers, is one layer of protection. Installing virus protection and detection on the firewalls and servers that integrate DER into the broader system of grid operation is another layer. This strategy for DER is complex, considering the number of owners, operators, and systems involved, but it’s crucial to reduce the chance of cyberattack.
The DOE Solar Energy Technologies Office (SETO) is working to ensure the electric grid is smart, secure, and capable of integrating more solar power systems and other DER. SETO has developed a Roadmap for Photovoltaic Cybersecurity, supports ongoing efforts in DER cybersecurity standards, and is involved in the Office of Energy Efficiency and Renewable Energy (EERE) Cybersecurity Multiyear Program Plan and DOE’s broader cybersecurity research activities.
Continue reading

Subscribe to our newsletter
Promotions, new products and sales. Directly to your inbox.